The increasing risks of cyber security breaches are very worrying for businesses and it is of utmost importance to do everything you can to protect against them. Having a plan in place is a great start.
Understand the risks associated with SME cyber security
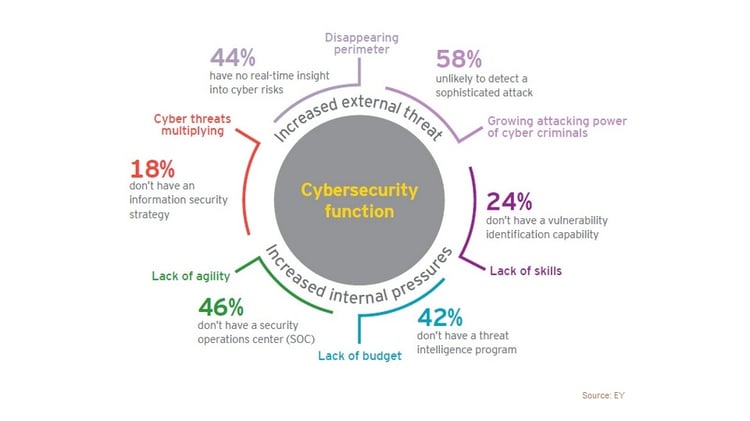
Understanding the variation of threats to your internet security is crucial to creating preventative strategies. Even small businesses are vulnerable to attack, in fact small businesses are often more vulnerable to attack because they don't have the same big budget for protection as large corporations.
Viruses can happen to any kind of organisation or individual, they are indiscriminate. Writing a security policy for your business is prudent. Ensure all employees are well versed in the policy and fully understand the implications of non-adherence.
Hacking
Breaches of your internet security can happen to anyone at any time. You also need a policy which indicates what to do if a breach occurs. If you are the victim of a cyber attack, you'll be glad to have a reference as to which systems need to be closed down and how to retrieve potentially lost data.
A hack attack is when someone gains entry into your system with the intention of accessing or stealing data that is saved there.
Malware
Malware can take the form of spying software, ransomware, viruses or worms.

Malware is potentially very harmful to your entire computer system. Once malware has been installed it can be used to access, monitor and steal files.
Phishing
Most people will have experienced phishing scams.

Some look more convincing than others. Phishing is when you are tricked into clicking on a website or email and then entering personal information. Criminals may pretend that they are from your bank, the tax office or other official body in order to con you into parting with sensitive details.
Leaks
Be aware that security risks can come from inside your company too. Employees who have access to valuable data may either be tricked into leaking data, or do so maliciously.

Manage this by ensuring that nobody has a higher level of access than necessary to files or servers. You can also use audit trails to ensure that people are accessing information appropriately.
DDoS
This stands for a Distributed Denial of Service attack.
In this scenario, cyberbots attack your server and cause it to shut down by pinging it continually.
Types of security
Secure individual devices, install software designed to protect businesses on each phone, PC and tablet and ensure that this software is always kept up to date.
Protect your network In addition to your business Wi-Fi, create a separate guest Wi-Fi for visitors.
Have a secure firewall and where possible, connect to the internet via Ethernet cable as this offers more protection than Wi-Fi.
Business broadband providers usually offer a good level of network security. Check what is included in your package and what else can be offered by your provider.
Hardware security
Anything that connects to your network is at risk so secure all of it. This includes tablet devices, mobile phones, storage drives and servers. Be particularly cautious about equipment that is used for remote access as accessing files and servers away from work has a higher level of risk attached. Provide employees with the necessary protection.
Password protection

Write a policy for creating passwords. Every password must be unique and strong. Long passwords are better than short ones so aim to use a minimum of 12 characters. Combine uppercase and lowercase letters and include symbols and numbers. It is genuinely important to avoid using the same password for more than one log in because if a cybercriminal gets hold of that password they can then use it to unlock any portal using the same details.
Of course, remembering a number of different passwords is easier said than done so try to use a system that is known only to you and is complex enough that a cyber criminal couldn't quickly crack your code. There are a number of apps that enable you to manage your password or you could also try using variations on a theme perhaps changing the last two letters of your standard password for each portal that you protect. If you have a team password for an account or file, then be sure to change this when an employee leaves the business.
.png?width=200&height=75&name=Amvia%20New%20Header%20Logo%20(11).png)


.png)